Is bringing your own device to work a bad idea?
Don’t Let BYOD Spell Disaster
As ‘Bring Your Own Device’ or BYOD rises in popularity, with more than two-thirds of us using a personal device at work, it’s important for businesses to understand the security risk that this can pose. Improperly managed devices can expose organisations to serious threats from both external bad actors and accidental or malicious insider risk. Here we’ll explore the potential risk and what you could do within your business to stop BYOD from spelling disaster.
A lot of companies proactively encourage their employees to use their personal devices to work outside of the office and why wouldn’t they? On average, employers allowing their staff to use their own laptop, tablet or smartphone gain an additional 240 hours per year of work time per employee and save money on hardware costs, yet only 39% of businesses have a formal BYOD policy – not ideal, right? Let’s look at why that might be… 
To BYOD or Not to BYOD?
Believe it or not, a lot of organisations don’t understand what their BYOD estate looks like. If you’re reading this and thinking ‘that sounds like me’, then trust me, you’re not alone! When I speak with clients, I always ask them about personal device usage within their business and a lot of the time I get blank stares. A lot of people haven’t thought about it, and where they have, they tend to have not considered that people accessing their e-mail from a smartphone also counts as a user bringing their own device… because everyone does that, right?
When deciding whether to allow users the opportunity to use their personal device, we need to make sure we’re weighing up the security risks versus the business benefits. And if we do decide that our users can access corporate data from a BYO device, then we should consider how much access we’re comfortable with them having.
The Risks
Generally speaking, when we have a corporate device estate, our IT team has some level of control over the endpoints – usually via a mobile device management (MDM) solution like Microsoft Intune, MobileIron, or AirWatch. So, when a user loses their device, the business can remotely wipe it and any corporate information is no longer accessible from that phone.
One of the main issues with BYOD is that organisations often lack control over that part of their estate. Users don’t want to sign up to policies where their employer can remotely wipe their entire personal device and if the organisation is unaware of alternative options, they may choose to not enforce any BYOD policy, meaning that when a personal device containing corporate information is lost, the corporate information is lost with it. Not good.
It’s not just control over the device that seems difficult with BYOD. It’s also control over the data. With a corporate device, users are free to copy data from one application to another, as the whole device is owned by the company. The waters muddy when we bring in personal devices with non-corporate applications. For example, if your sales team is given access to your CRM system on their own phones, what’s to stop them copying and pasting the data out of there and into the Notes app or a Google Sheet? Usually, the answer is ‘very little’! 
Finally, working in security, we know that patching should be our number one priority. And with corporate devices, it usually is. But do our end users understand the importance of it? Probably not! So with BYOD, we’re often faced with allowing our users to access our corporate network, data and resources from an unpatched device which doesn’t necessarily have all of the security controls, such as passcodes, that we would usually enforce.
So what should we be doing?
The Mitigation
Well the first thing we should do is look to implement a BYOD policy. Undoubtedly within the business there will be users wanting to access (or more likely, already accessing) their work e-mail, contacts, and potentially applications from their own laptops, tablets and smartphones. Having a policy in place which covers what we expect of our users in terms of patching, device security and data usage is a good first step.
Communicating this policy and ensuring that users have understood the implications will, in itself, help to improve security. Users don’t inherently want to jeopardise our security strategy (although it does sometimes feel that way), so driving awareness should bring rewards.
Next, we should look at what we can do with our (hopefully pre-existing) MDM solution to protect our corporate data on personal devices. For users of Microsoft Intune, App Protection Policies are a great place to start, allowing organisations the ability to block copy-paste of data between corporate and personal applications, and providing a selective remote wipe function for when devices are lost or the user leaves the business. 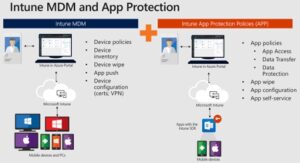
For Android users, the use of the “Work Profile” feature will potentially be useful to allow people to split their corporate and personal applications, making them less likely to accidentally share data, as well as driving a better work/life balance with the ability to switch off the work profile after-hours or on weekends.
I’d also recommend that organisations look to gain an understanding of the type of data that bad actors could access if a device were to be lost or stolen. Undertaking a lost or stolen device assessment will provide an insight into exactly how far an attacker could get, which systems could be compromised and a set of recommendations for improvements to be made for better device security.
It’s always recommended that when we complete this type of assessment, companies provide an entire laptop bag including any notebooks, etc. that a user usually carries around. This ensures that we have a more realistic view of the information that a hacker would have access to and can therefore provide a wider and more detailed set of recommendations for improving device security.
So, when considering allowing users to access corporate data from their personal devices, there are a few things to consider and it’s important for you to weigh up the business benefits versus the security risks. If you’re interested in discussing further how we can support you in improving device security or would like to know more about a lost or stolen device assessment, get in touch with us: sales@cognisys.co.uk!
Statistics: 41 BYOD Stats for 2020 [67% of Us Are Doing It] (techjury.net)


