Cloud penetration testing
Strengthen your cloud security with Cognisys. Protect your data, ensure compliance, and mitigate the risks of insider threats with our cloud penetration testing.
Secure your cloud infrastructure against insider threats
In today’s multi-cloud world, securing your cloud environment from social engineering and internal conflict is critical, but can be complex to do internally without bias and blind spots.
Cognisys offers in-depth cloud penetration testing designed to simulate insider threats, such as rogue or compromised employees, using white-box credentials to assess vulnerabilities across AWS, Azure, and Google Cloud Platform (GCP). Our experts employ thorough techniques to mimic potential attack scenarios, aiming to exfiltrate sensitive example data, such as emails and files, while identifying weaknesses in your cloud security posture.
What we test
Infrastructure security
We assess the security of your cloud set-up, including firewalls, virtual networks, and access controls, to ensure robust defences and compartmentalisation are in place.
Identity & access management (IAM)
Evaluation of IAM policies to prevent unauthorised access, ensuring that only the right users have access at the right time.
Data protection
Testing encryption methods, data storage configurations, and access controls to prevent breaches.
Compliance & governance
Verifying that your cloud environment meets industry standards and regulatory requirements, ensuring compliance with frameworks such as GDPR, HIPAA, and PCI DSS.
Incident response capabilities
Simulating insider threats to test your organisation’s ability to detect, respond, and recover from malicious activities within your cloud infrastructure.
Misconfigurations & human errors
Identifying potential vulnerabilities arising from misconfigurations, insecure interfaces, and human errors are familiar yet critical factors in cloud security risks.
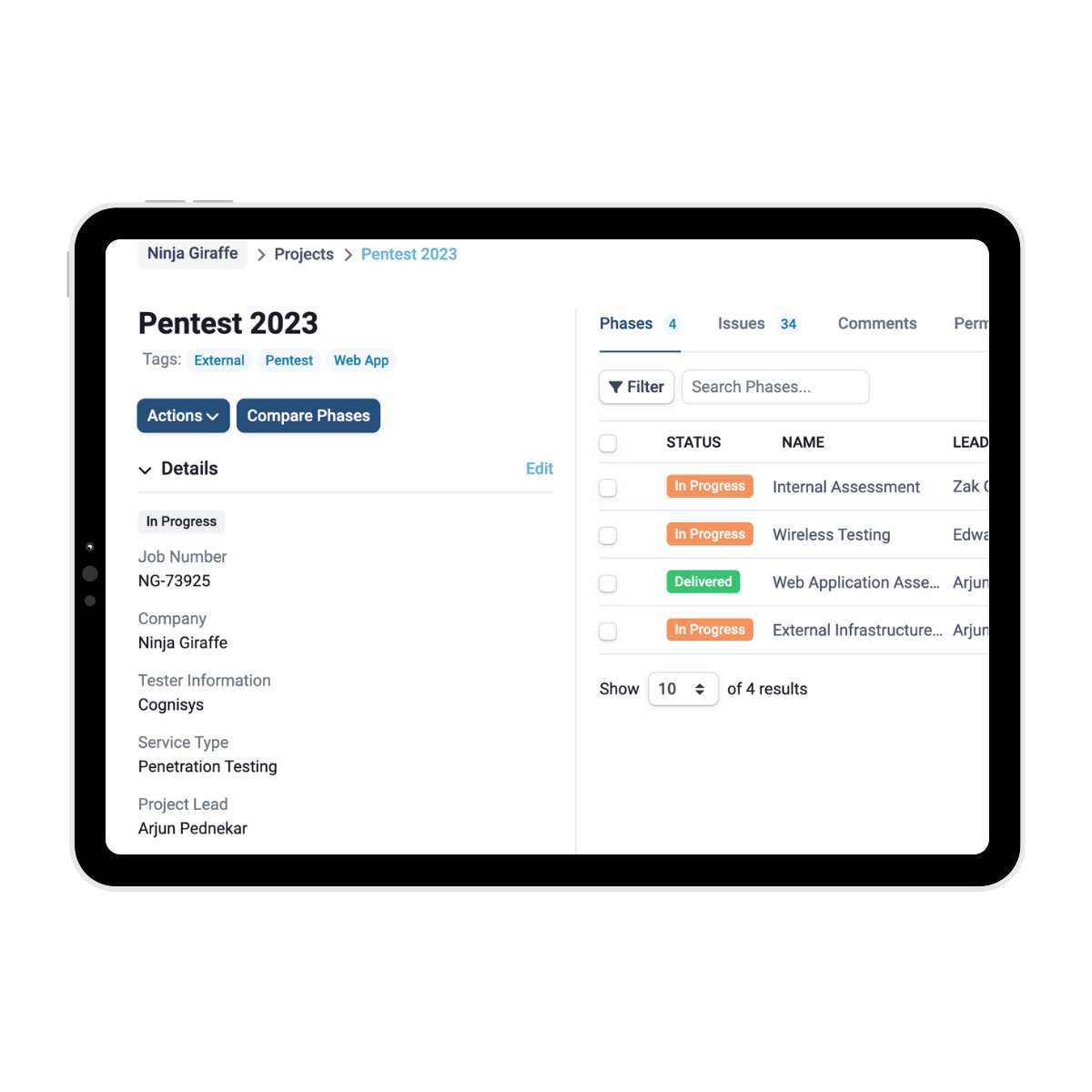
SmartView takes care of your reporting
Cognisys’ SmartView Portal provides a centralised platform for clients to manage their projects and vulnerabilities efficiently. Through the portal, clients can track the status of each identified issue, assign tasks to team members, and monitor the progress of remediation efforts. This streamlined process ensures that vulnerabilities are addressed promptly and thoroughly, enhancing clients’ cloud security.
Why choose Cognisys’ cloud penetration testing?
Our expert testers, skilled in maintaining, reading, and breaking enterprise environments, tailor simulations to mirror real-world insider threat scenarios by closely collaborating with your IT team. After testing, we provide detailed reports identifying vulnerabilities, their impact, and practical remediation steps.
Additionally, we offer expert guidance during a post-test wash-up call to help your teams implement effective solutions. With experience across all major cloud platforms, including AWS, Azure, GCP, and internal systems, we ensure a comprehensive evaluation of your cloud infrastructure’s security.
FAQs
Let’s make things happen
Fill in the form and one of our team will be in touch for a no-obligation discussion or quote regarding your requirements.
info@cognisys.co.uk
Leeds office
5 Park Place
Leeds
LS1 2RU
info@cognisys.co.uk
London office
131 Finsbury Pavement
London
EC2A 1NT