How does a password cracking assessment work?
Our password cracking assessment provides insight into the effectiveness of your organisation’s password policy by analysing password hashes from your Security Accounts Manager (SAM) file. By leveraging our advanced cracking machines, we evaluate password strength and provide detailed results, highlighting weak or compromised passwords.
This service helps you identify vulnerabilities in your current password policy, offering actionable recommendations to improve password security across your organisation.
Methodology
Secure transfer of SAM hash file
We ensure a secure, encrypted transfer of your SAM hash file using trusted methods like our secure file transfer on SmartView. This prevents interception or tampering during the transmission of sensitive data.
Password hash analysis
Once the SAM hash file is securely received, we initiate a thorough analysis using industry-standard cracking algorithms and techniques. Our high-performance cracking machines run through extensive wordlists, brute force, and dictionary attacks.
Multi-phase password cracking
We execute password cracking in multiple phases, starting with the simplest and most common password variations. We progressively move to more complex attacks, ensuring a comprehensive assessment of password strength.
Assessment of cracked passwords
Our team analyses the cracked passwords to identify trends, such as weak password patterns, reused passwords, and any non-compliance with organisational policies. This helps pinpoint the specific vulnerabilities in your current password policy.
Secure reporting
Once the assessment is complete, we compile a detailed report outlining the cracked passwords, the time to crack them, and insights into policy weaknesses. This report is securely delivered using encrypted channels to maintain data confidentiality.
Actionable recommendations
Based on the findings, we provide recommendations to enhance your password policy. This includes implementing more robust password requirements, adopting multi-factor authentication (MFA), and training employees on best practices for password management.
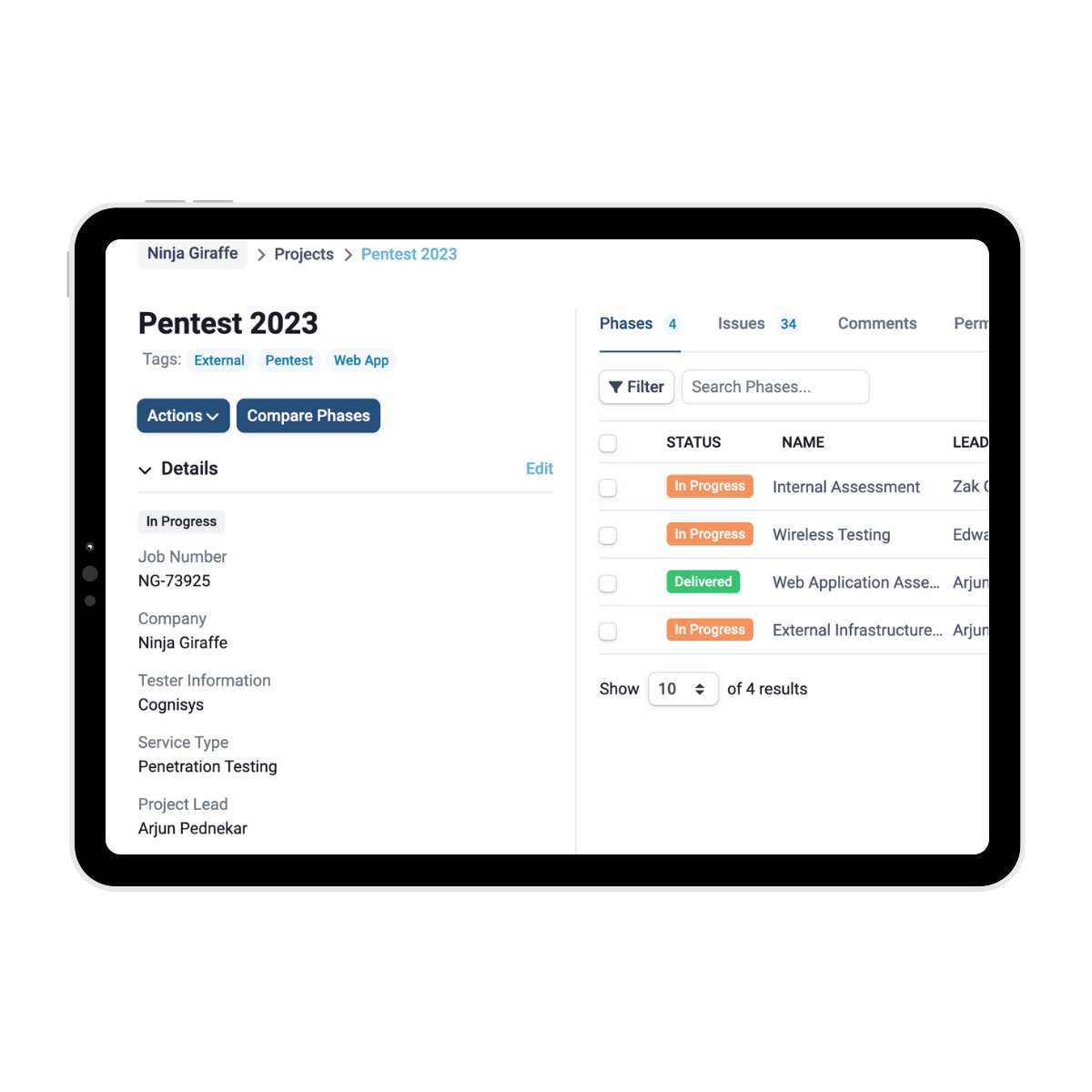
SmartView takes care of your reporting
Cognisys’ password cracking service provides clients with a detailed statistical report through the SmartView Portal, a centralised platform for efficiently managing projects and vulnerabilities. The report highlights key metrics such as cracked password percentages, common patterns, weak credentials, and time to crack.
Clients can track findings, identify security gaps, and assign remediation tasks directly within the platform. SmartView offers real-time insights and a streamlined workflow, enabling clients to reduce risks, strengthen password policies, and improve security posture.
Why choose Cognisys’ password cracking assessment?
We bring extensive expertise in password security and cryptography, leveraging years of experience to provide precise and thorough assessments. Using cutting-edge password-cracking technology and high-performance machines, we ensure comprehensive and efficient testing.
Our commitment to security is paramount, ensuring the safe transfer of your sensitive data and delivering encrypted, secure reports. Unlike generic solutions, our recommendations are tailored specifically to your organisation’s needs, offering actionable insights to strengthen your password policies. With a proven track record of helping organisations improve their security posture, we are dedicated to delivering results that enhance your long-term protection and success.
FAQs
Let’s make things happen
Fill in the form and one of our team will be in touch for a no-obligation discussion or quote regarding your requirements.
info@cognisys.co.uk
Leeds office
5 Park Place
Leeds
LS1 2RU
info@cognisys.co.uk
London office
131 Finsbury Pavement
London
EC2A 1NT