Go Phish: A Guide to Phishing Scams
Phishing is possibly the most common type of cyberattack, being the vehicle for credential theft and malware distribution. It first appeared on the scene in the 80s and has grown exponentially since then, with over 40,000 unique phishing campaigns reported by research organisation APWG each month. Worryingly, 97% of users would be unable to detect a sophisticated phishing attack, so what do we need to look out for? And how can we protect ourselves?
Go Phish!
The word phishing is a “catch-all” term for fraudulent activity designed to capture credentials, credit card details or other sensitive information. It may also mean the mechanism by which an attacker distributes malicious content to infect a device or network with ransomware, usually via an e-mail attachment.
We’ve probably all been the target of a generic consumer phishing campaign, with messages supposedly from Amazon, Netflix, or our e-mail providers asking us to reset our passwords. These are usually poorly designed messages, sent en masse to hundreds or thousands of users, from attackers expecting a low success rate. Fortunately, the majority of these types of phishing messages are filtered by our default e-mail security settings and those that do make it through are often easily identified, but more on that later!
As we’ve grown more security savvy, criminals have had to develop more sophisticated attack techniques. In a business context, attackers often choose specific individuals or teams within an organisation to target in a technique known as spear phishing. As businesses tend to have more complex security technologies, their phishing e-mails need to be more realistic in order to bypass layers of defence and convince the end-user of the veracity of the message.
Often, the attacker will research the organisation or individual via social media and the web to allow them to craft a specific message that will resonate with the user, be that with a “free offer” for a place the person is known to frequent, something specific to their role in the business, or an e-mail supposedly from the IT team asking them to input credentials to a “corporate” system. Where this type of attack is aimed at a senior executive or director within the organisation, it is known as whaling, as they’re a much bigger target.
E-mail is not the only medium that phishers use to harvest information. Other methods include voice phishing, also known as vishing, whereby hackers generate an automated message impersonating an institution like HMRC, usually designed to get people to hand over credit card information; SMS phishing, or smishing, with criminals purporting to be a legitimate organisation (often a network provider) and getting users to click on links within a text message, in the hope of getting user credentials; and notification phishing, with notifications popping up on your phone or in your inbox from corporate or consumer applications containing malicious links for credential theft.
No Phish!
As with any other type of attack, the best way we can protect ourselves is to reduce our attack surface. In this instance, it means that we should be trying to filter out malicious content and links before they reach our end users, meaning that they no longer have the responsibility for identifying nefarious messages. Most e-mail providers include a free message filtering service, for example, Exchange Online Protection, but in a corporate environment, it’s wise to introduce a further layer of defence with a solution like Mimecast or Microsoft Defender for Office 365.
However, we know that technology isn’t always fool-proof, and with the number of phishing campaigns rising on a monthly basis, it’s important that we help our users how to spot potential threats, via user awareness training. For larger organisations, it might be helpful to understand which teams or users need the most help with this, so completing a phishing simulation to monitor click-throughs etc, can help to identify the weaker links in your security chain.
If users do happen to give away their credentials, then having multi-factor authentication (MFA) enabled could be your saving grace. Switching on MFA means that users need to provide a second factor of authentication to verify their identity, so an attacker who does have a corporate username and password into your environment will still be stopped at the first hurdle when they’re unable to authenticate with a text message, phone call or authenticator application tied to the real user’s mobile phone or personal e-mail address.
What to Watch Out For
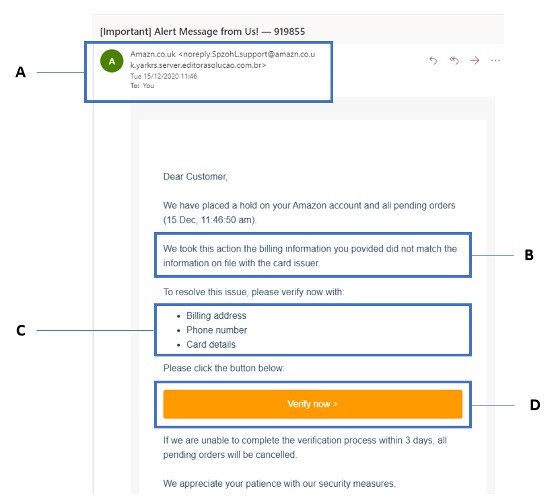
There are many things we should look out for when we see a phishing e-mail. I’ve taken this one from my own inbox and have highlighted some of the key things we should be checking when we get a suspicious e-mail.
The first thing to check with any e-mail we get is where it’s come from. If we look at section A on the above image, the sender has named themselves ‘amazn.co.uk’. Not all e-mails will have an obvious spelling mistake like this one, but illegitimate messages will have an e-mail address that does not correspond with the supposed sender.
A lot of bulk phishing e-mails have spelling mistakes. The reason for this is that often the people who would respond to an e-mail littered with bad grammar and spelling are gullible enough to also provide the data wanted by the criminals, as we can see in section B of the example e-mail. Spelling mistakes are commonplace in wide net phishing, but it is important to note that spear-phishing / whaling campaigns are much more sophisticated and use well-crafted messages to convince their victims.
Hackers often ask for sensitive or financial data (section C), such as personal details or credit card information. Most larger organisations now have a policy of never asking for personal information in e-mail or on the phone, so when we see this type of request in an email message, we should be on high alert!
Finally, we should always be verifying links before clicking on them (section D). Hackers embed links to credential harvesting websites which are mocked up to look legitimate but in fact allow users to submit their usernames and passwords to a database owned by the attackers. Always hover over links before clicking on them to ensure that they direct to a legitimate website, and if in doubt, search for the real website using your internet browser. In this example, the link did not connect to Amazon and instead redirected to this website: https://journal.biotrop.org/public/.
So, with phishing set to stay with us, it’s important that we ensure our users are vigilant in their search for malicious content and they know the signs to look out for. Users are the first line of defence for our security estate and yet often represent the biggest weakness for us – ensuring they have the knowledge to understand what a phishing e-mail looks like, how to report one and what they should and should not do with a potentially risky message can be the difference between a breach and no breach. For more information on protecting your organisation against phishing threats, and to discuss our phishing simulation engagements, get in touch with us at sales@cognisys.co.uk.



