How to protect against AiTM/Evilginx phishing attacks
A deep dive into the Attacker-in-the-Middle (AiTM) threat, spotlighting EvilGinx2. Discover how to protect against phishing and thwart AiTM attacks with essential strategies.

Zak Clifford
13th March 2024
Heyy, it’s me, Zak! In this blog, we’re going to take a close look at a specific phishing technique that’s been causing quite a stir: the Attacker-in-the-Middle (AitM) attack, with a focus on the tool known as EvilGinx2.
EvilGinx2 is an advanced phishing tool that can sneak past two-factor authentication, posing a significant threat to even the most vigilant users. But there’s no need to worry. In this post, I’ll explain what AiTM and EvilGinx2 are and provide you with three different methods to counteract these attacks. Stay with me as I guide you to enhance your cyber security.
What is AiTM/Evilginx?
To thwart EvilGinx, it’s key to know how it operates. Threat actors buy a deceptive domain and trick users into visiting it, which then forwards them to the real Office 365 login page. The attackers capture authentication tokens after login, allowing unauthorised access to Office 365. Despite evading detection by several Microsoft security tools, we found methods to block EvilGinx.
EvilGinx bypasses SSL errors by initiating a new SSL session with Microsoft’s login page, which seems beneficial to attackers but is actually their downfall. Microsoft Entra Conditional Access detects and blocks EvilGinx2 by checking additional security measures such as IP address, domain membership, device compliance, and certificates.
Currently, there are three main open-source AiTM phishing kits available that are widely known:
Scenario
Scenario
Imagine that Bob, an employee at a mid-sized corporation, receives an unexpected email one morning. The email, which appears to be from the company’s IT department, warns him that his password is due to expire in 24 hours and he must login to his account via the link in the email immediately to avoid any disruption to his access. Concerned about losing access to his emails, Bob clicks on the prominently displayed “Reset Password” link in the email.
The link redirects him to a login page that closely resembles the company’s official login portal. Without hesitation, Bob enters his current username and password, believing he is following standard procedure. After submitting his credentials, the page redirects him to his mailbox.
However, unknown to Bob, the email was a sophisticated phishing attempt, and he has just provided his credentials to an attacker using an AiTM phishing kit like EvilGinx2. The threat actor captures his email address and password, and MFA code, along with the session tokens. With the session tokens, they gain unimpeded access to Bob’s email account, potentially compromising sensitive corporate data and causing significant security breaches.
This scenario highlights the effectiveness of AiTM phishing attacks and the importance of implementing strong Conditional Access policies to prevent unauthorised access, even when credentials are compromised.

Recommendations
Recommendations
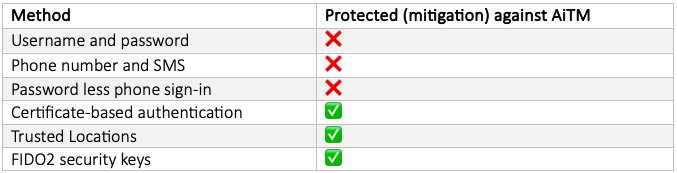
Here are three recommendations which would help to thwart this type of attack. Beginning in report-only mode or initially deploying to administrators can be an effective strategy, given the exceptional flexibility of Conditional Access. Below are some authentication methods that can and cannot protect against AiTM.
To bolster your organisation’s defences against AiTM/Evilginx phishing attacks, implementing robust Conditional Access policies is essential. Here are three recommendations that can significantly enhance your protection against the attacks.
1. Conditional Access -Trusted locations only
By setting up Conditional Access policies that restrict access to your cloud apps based solely on trusted locations, you create a digital perimeter around your data. This approach leverages the geographical security boundaries that you define as ‘trusted’. Any login attempt originating from outside these locations will be automatically blocked, thereby neutralising the threat posed by AiTM attacks that rely on access from untrusted regions. This method is particularly effective when attackers are known to operate from specific parts of the world.
2. Conditional access – Intune Device Compliance
This recommendation ensures that only devices deemed compliant by Microsoft Intune can access your cloud applications. Intune assesses devices against your organisation’s security requirements before granting access. If a device doesn’t meet these standards, it’s barred, preventing compromised devices from being used in an AiTM attack. This measure is a critical component of a defence-in-depth strategy, ensuring that both user identity and device health are verified before access is granted.
3. Conditional access – Fido2 Security Key (URL Binding)
FIDO2 security keys provide a form of phishing-resistant MFA, which is essential in the fight against AiTM attacks. By requiring users to authenticate with a physical security key that is bound to the original URL, you eliminate the risk of attackers intercepting credentials or tokens. This method ensures that even if users are tricked into visiting a fraudulent site, the security key won’t work, as it’s not associated with the deceptive domain. This is an advanced level of security suitable for protecting high-value accounts, especially administrative ones, where the impact of a breach could be particularly severe.
Implementing these Conditional Access recommendations will put your organisation in a strong position to defend against AiTM and Evilginx2 attacks. Each recommendation targets a different aspect of the attack vector, from location-based access control to device compliance and hardware-bound authentication. By deploying these measures, you can ensure that your defences are not only robust but also multi-faceted, addressing the complex nature of modern cyber threats.
The settings of each conditional access policy are outlined below:
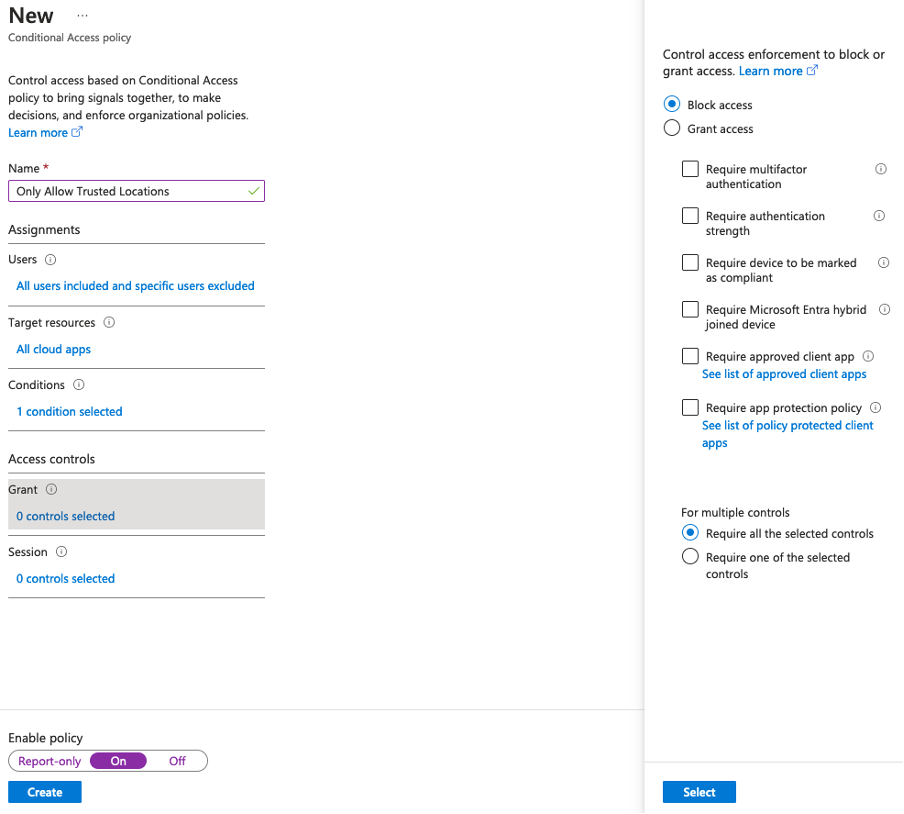
1. Conditional Access – Trusted Locations Only
Users: ALL (Exclude Break Glass Accounts)
Target Resource: All Cloud Apps
Conditions: Any location and all trusted locations excluded
Grant: Block Access
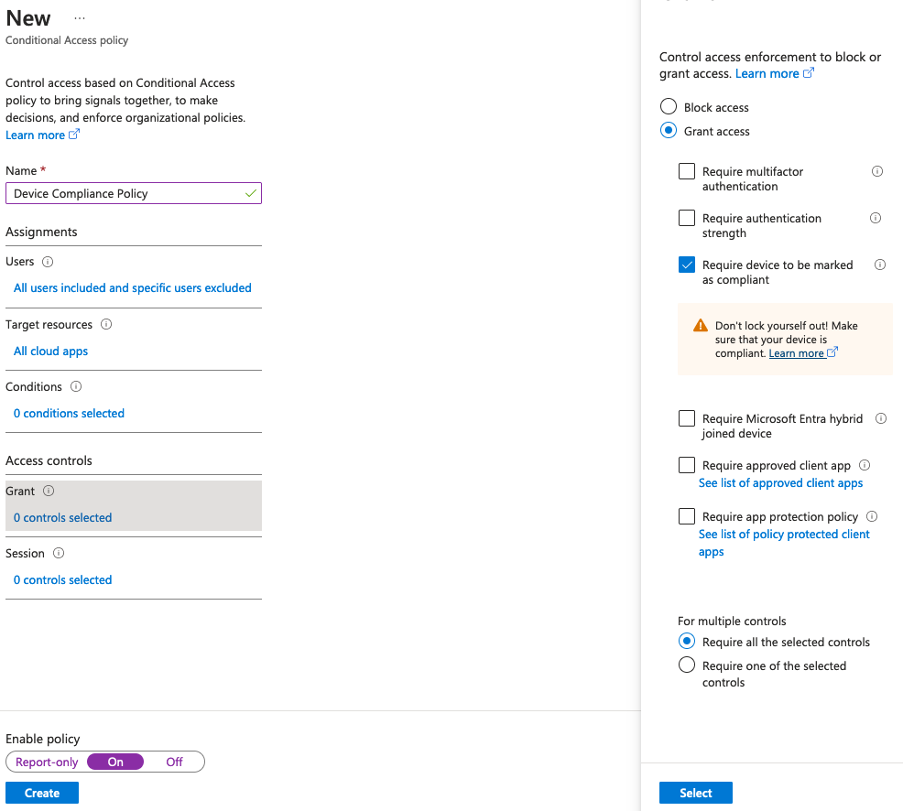
2. Conditional Access – Intune Device Compliance
Users: ALL (Exclude Break Glass Accounts)
Target Resource: All Cloud Apps
Conditions: 0 Conditions
Grant: Require device to be marked as compliant
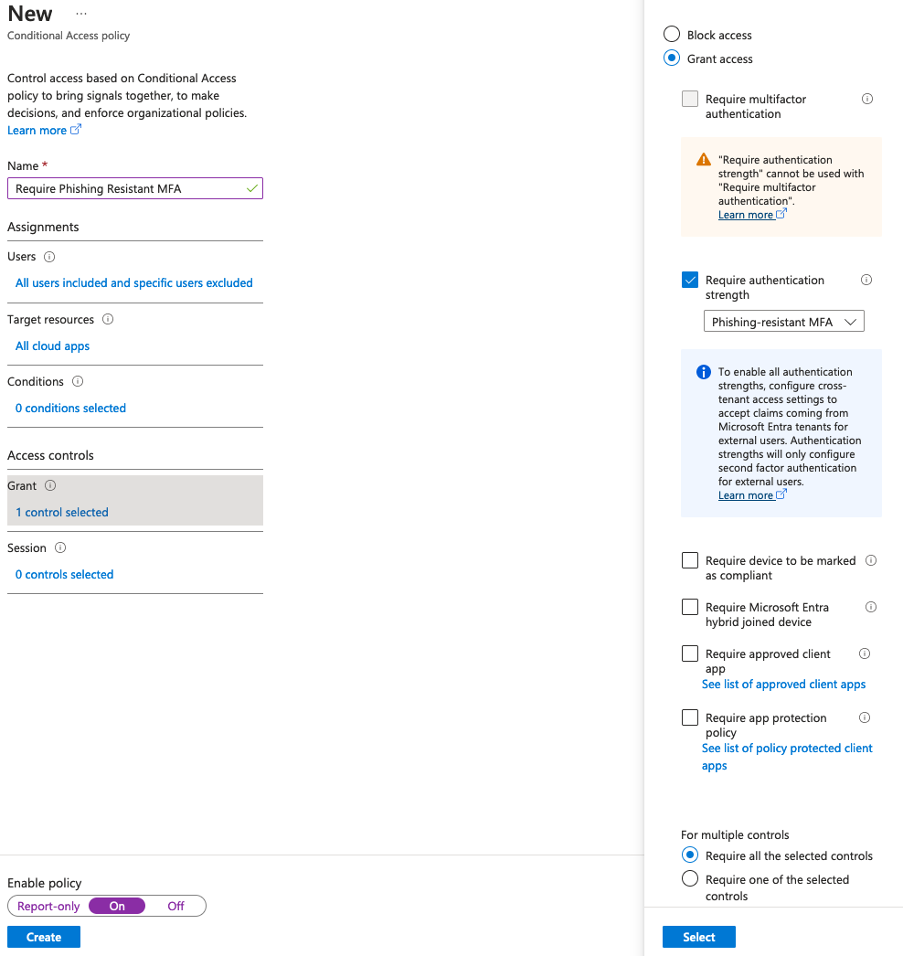
3. Conditional Access – Fido2 Security Key (URL Binding)
Users: ALL (Exclude Break Glass Accounts)
Target Resource: All Cloud Apps
Conditions: 0 Conditions
Grant: Require authentication strength: Phishing Resistant MFA
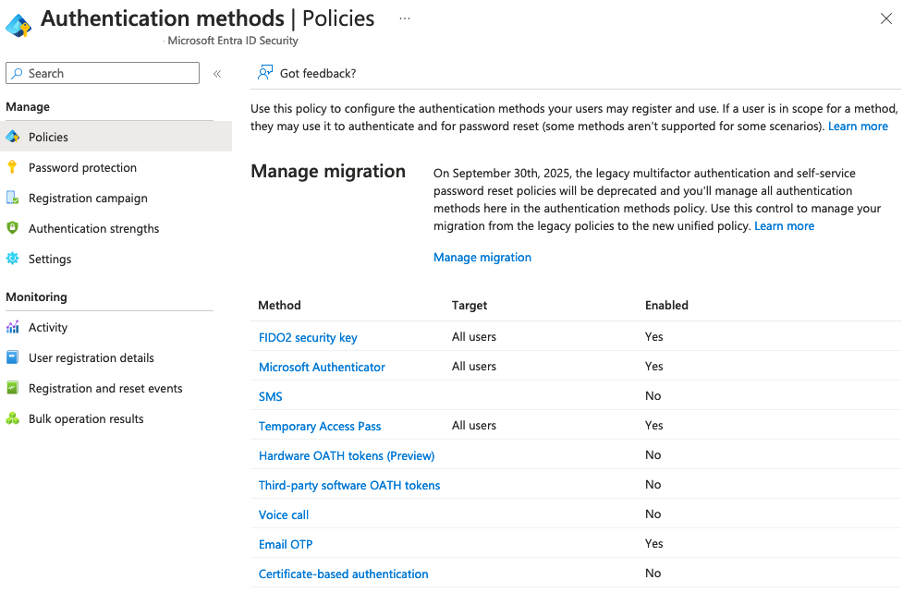
Ensure that the authentication method is enabled as seen below:
Conclusion
Conclusion
It’s crucial to maintain proactive defences such as employee education and securing email and web gateways, as these can thwart numerous attacks from the outset.
Conditional Access stands out as a powerful tool in the fight against contemporary cyber threats, offering a range of customisable policies and rules tailored to an organisation’s needs.
For businesses primarily using Intune or Entra for device management, bolstering security against modern threats can be accomplished with relative ease.
Phish-resistant MFA emerges as a key player in defence strategies especially for admin users, but adoption may be gradual.
If you’d like to know how susceptible you are to a phishing attack, get in touch and we can provide a simulated phishing attack to test your defences.