New critical SSH vulnerability released
In this blog, we cover the new SSH vulnerability CVE-2024-6387 (“regreSSHion”), its impact, and essential actions to secure your systems.
CVE-2024-6387 overview
On Monday, the 1st of July, you may have seen that a new SSH vulnerability was released, termed “regreSSHion,” and labelled as CVE-2024-6387. The re-introduction of a previously patched OpenSSH vulnerability allows for unauthenticated remote code execution. It affects OpenSSH versions from 8.5p1 up to but does not include 9.8p1 for public-facing servers. Immediate attention and action are required to secure your infrastructure. Detailed technical details about this vulnerability are available in the Qualys report here.
However, here are the top takeaways:
- This affects Linux and macOS systems as OpenSSH is a standard program they use.
- The primary threat is to public-facing servers running the above OSs.
- No public POCs currently exist, but independent researchers report they have been able to reproduce the CVE.
- Current estimates are that it takes 6-8 hours of constant requests to achieve exploitation.
- Because of the large number of request tries required for exploitation, tools like Fail2Ban are expected to provide adequate protection until patches can be applied.
Cognisys’ SmartScan customers were contacted yesterday, informing them of the vulnerability and if their assets were affected.
If you would like more information on this new threat or any other cyber security concerns, we are happy to help.
Recommended actions
1. Immediate patching
- Update OpenSSH to the latest version that addresses this vulnerability.
- Follow the instructions provided by your Linux distribution for updating OpenSSH.
2. Temporary mitigations
Fail2Ban configuration:
- Install and configure Fail2Ban to block IP addresses that show malicious signs, such as too many password failures.
- Example configuration for /etc/fail2ban/jail.local:

Disable root login:
- Modify /etc/ssh/sshd_config to disable root login.
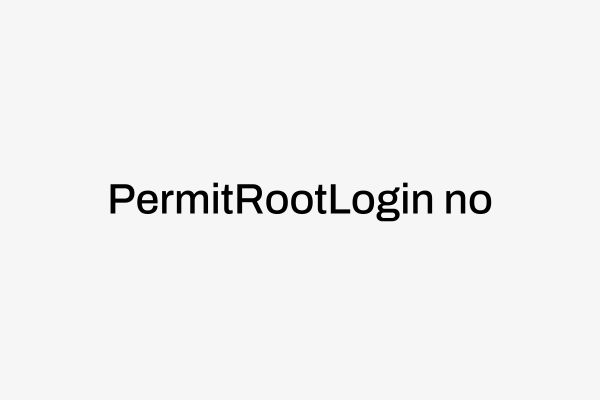
- Restart the SSH service: sudo systemctl restart sshd
3. Network restrictions
- Restrict SSH access to trusted IP addresses using firewall rules.
- Example using iptables:

4. Monitoring and logging:
- Enable detailed logging for SSH and monitor for unusual activity.
- Regularly review logs for unauthorised access attempts.
For more detailed information, please refer to the official Qualys blog post.
Cognisys CVE Checker Tool release
Members of Cognisys technical team have created a python script that can be used to detect external and internal facing assets that are running likely vulnerable versions of OpenSSH.
More details can be found here – https://github.com/CognisysGroup/CVE-2024-6387-Checker
To run the tool, simply execute the following:
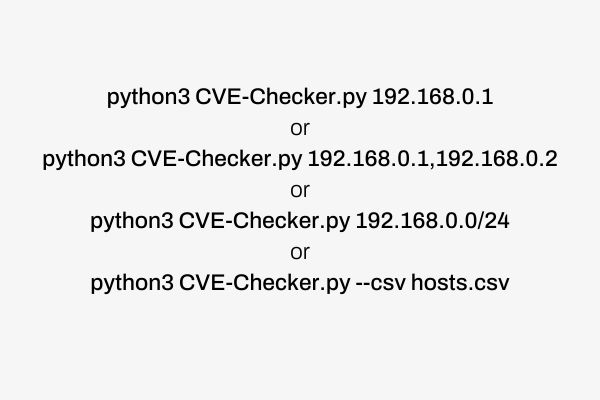
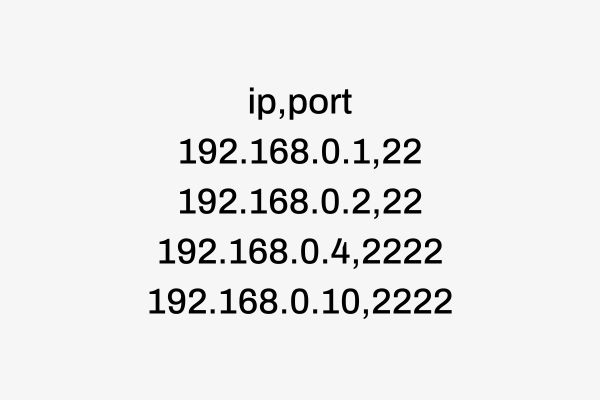
The csv should look something like:
Thanks for reading and stay secure.



