Why perform a cloud benchmark review?
In today’s rapidly transforming cloud landscape, benchmarking and road mapping a secure and compliant cloud environment is crucial.
The cloud benchmark review offers a structured assessment aligned with the Center for Internet Security benchmarks, designed to identify internal risks, misconfigurations, and compliance gaps in your cloud infrastructure. Cognisys’ service provides the insights and expert guidance to secure your cloud environments, ensuring they meet industry best practices.
Key elements of the service
Define objectives
We collaborate with your IT team to define the goals of the cloud benchmark review, focusing on specific security and compliance needs across your enabled AWS, Azure, and Google Cloud set-up. Whether you’re targeting particular controls or seeking a comprehensive assessment, we tailor our approach to your objectives.
Assess cloud environment usage
We identify which features, licenses and configurations are actively used in your cloud environment. This ensures that our assessment is focused on relevant areas and that the remediation advice aligns with your future goals and budget.
Access requirements
Our review process requires appropriate access permissions, typically read-only, to assess configurations without disrupting your operations. We ensure that all access is granted in a way that avoids conflicts with your existing authentication and device management policies.
Multi-cloud security evaluation
Our evaluation spans AWS, Azure, and GCP and covers identity and access management, network security, data protection, and compliance. We assess your cloud environments against the latest benchmarks, identifying potential risks and areas for improvement.
Industry-specific focus
We understand that each industry has unique security challenges and compliance needs. Our review is customised to align with your sector’s specific regulatory requirements and threat landscapes, whether it’s finance, healthcare, or another industry.
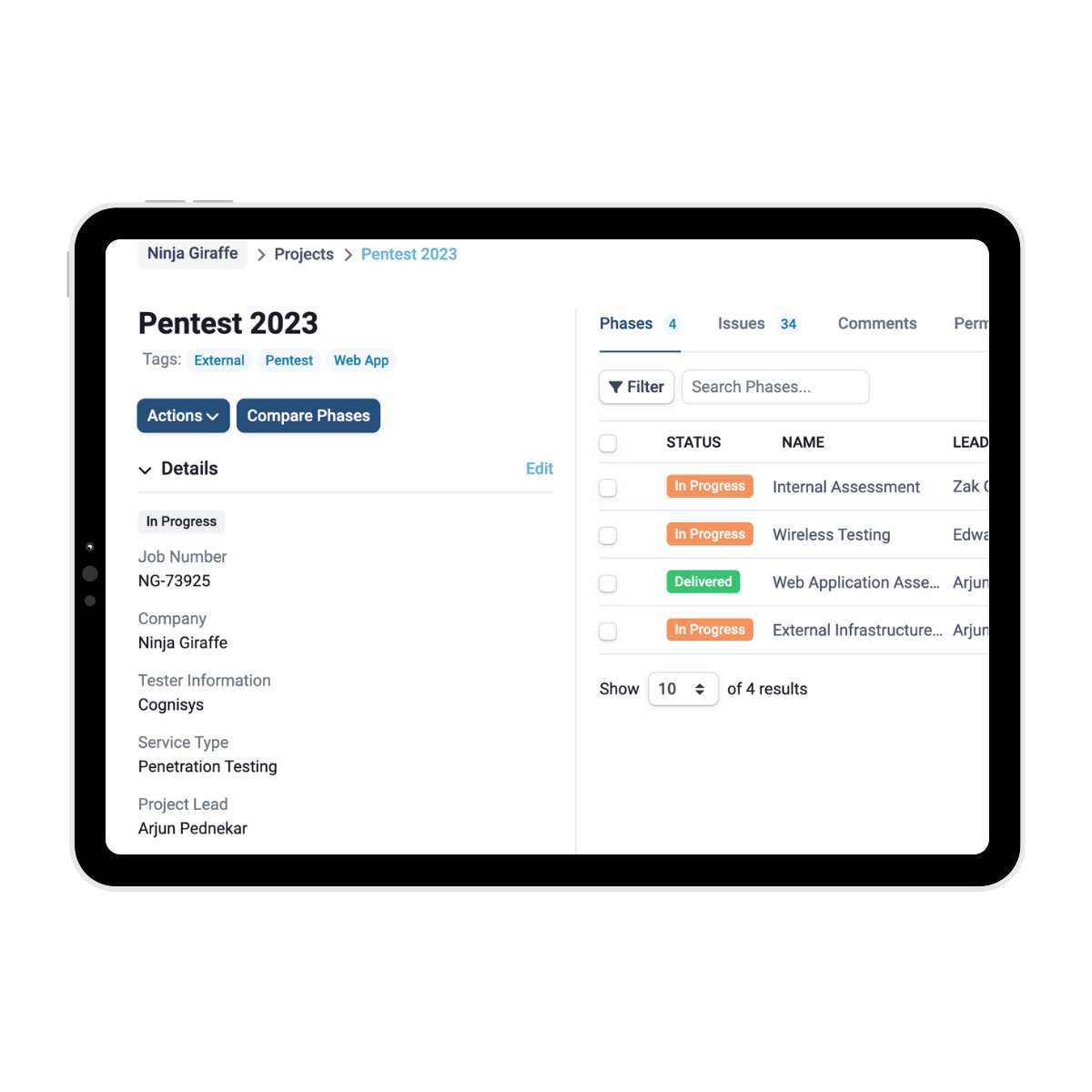
SmartView takes care of your reporting
Cognisys’ SmartView Portal provides a centralised platform for clients to manage their projects and vulnerabilities efficiently. Through the portal, clients can track the status of each identified issue, assign tasks to team members, and monitor the progress of remediation efforts.
A detailed report is prepared once the cloud benchmark review is complete, prioritising findings and providing strategic, actionable recommendations to strengthen your cloud security posture through our SmartView portal.
Why choose Cognisys for your cloud benchmark review?
By choosing our cloud benchmark review, you’re partnering with a team of experts who have experience building, maintaining, and penetrating a multitude of cloud and enterprise environments. We provide actionable, reasonable goals that go beyond identifying issues. We guide you through benchmark best practices and remediation, helping you maintain a secure and compliant cloud environment.
FAQs
Let’s make things happen
Fill in the form and one of our team will be in touch for a no-obligation discussion or quote regarding your requirements.
info@cognisys.co.uk
Leeds office
5 Park Place
Leeds
LS1 2RU
info@cognisys.co.uk
London office
131 Finsbury Pavement
London
EC2A 1NT