Why conduct external infrastructure penetration testing?
Conducting an external infrastructure penetration test is critical for identifying vulnerabilities in systems exposed to the internet, such as web servers, firewalls, and DNS configurations.
These tests help organisations detect potential entry points threat actors could exploit, including outdated software, misconfigurations, and weak security controls. By regularly evaluating external-facing assets, organisations can proactively strengthen their defences, reduce the risk of breaches, and ensure compliance with industry regulations.
Scoping and planning
Understanding business objectives
In the initial phase, we work closely with the client to align the external infrastructure penetration testing with their security concerns and business objectives. This involves identifying critical assets, understanding compliance requirements, and determining the focus areas of external-facing systems that potential threat actors could target.
Defining the scope
Once the objectives are established, we define the scope of the testing, which includes external IP addresses, web servers, firewalls, and other internet-facing infrastructure. Ensuring that all critical components are included is essential for delivering a thorough evaluation and identifying any boundaries or exclusions for clarity.
Rules of engagement
Next, we establish clear rules of engagement to guide the testing process. This includes the testing methods, tools, and techniques used. Additionally, we agree on operational guidelines, such as testing windows, communication protocols, and how sensitive findings will be handled to minimise disruption.
OSINT (Open Source Intelligence)
We perform OSINT to gather publicly available information about the client’s external assets. This step helps us identify exposed systems, domains, and other crucial details, such as leaked credentials from the dark web and publicly exposed unprotected cloud storage that threat actors could leverage, providing a clear map of what’s visible and vulnerable from an external perspective.
Threat landscape analysis
We perform a threat landscape analysis to make the testing more targeted, reviewing common external threats and vulnerabilities pertinent to the client’s industry and infrastructure. The testing scenarios are then tailored to simulate real-world attack methods, such as port scanning, web application exploitation, and network attacks.
Reporting
A detailed report is prepared once the testing is complete, prioritising findings and providing strategic, actionable recommendations to strengthen the external security posture through our SmartView portal.
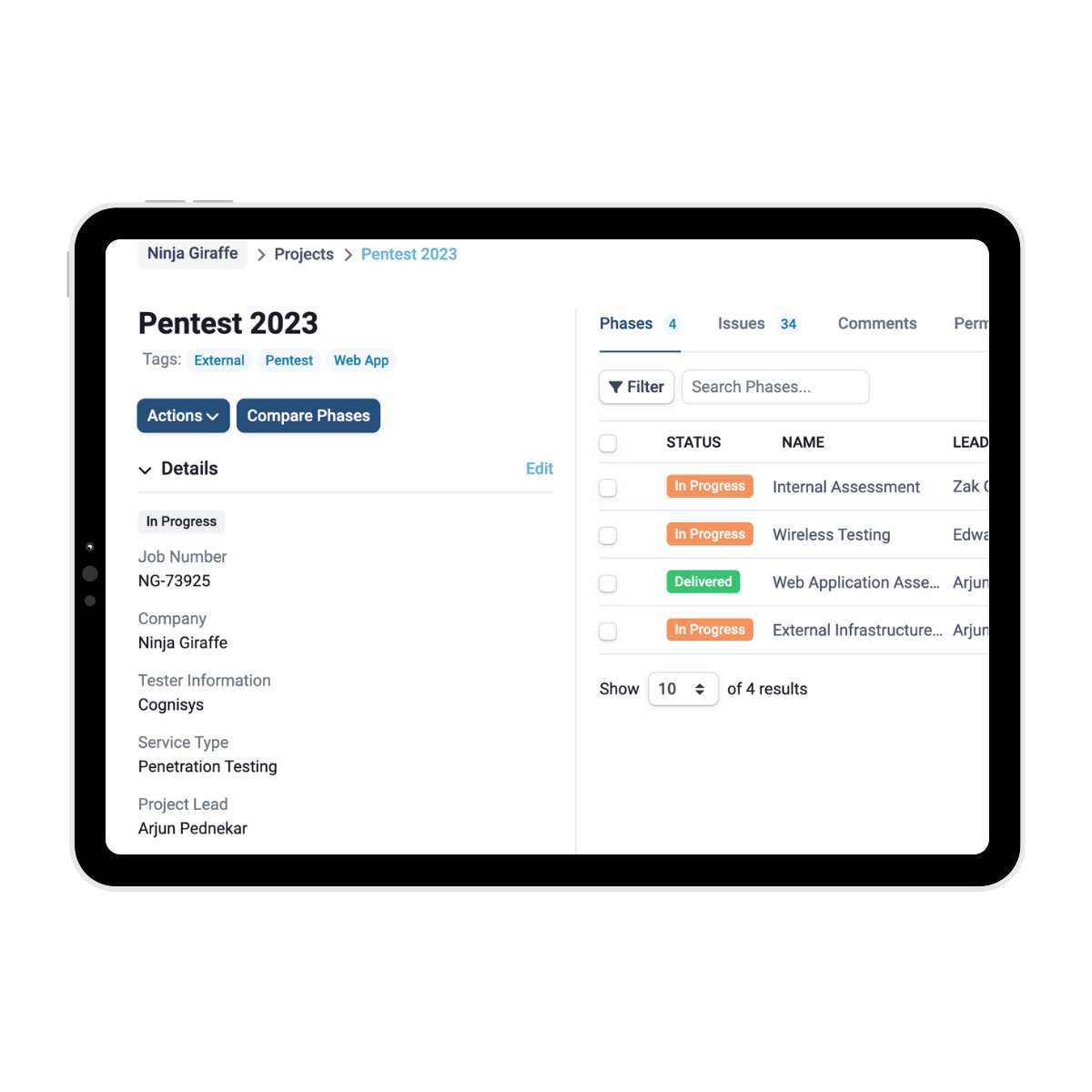
SmartView takes care of your reporting
Cognisys’ SmartView Portal provides a centralised platform for clients to manage their projects and vulnerabilities efficiently. Through the portal, clients can track the status of each identified issue, assign tasks to team members, and monitor the progress of remediation efforts.
A detailed report is prepared once the external infrastructure penetration testing is complete, prioritising findings and providing strategic, actionable recommendations to strengthen the external security posture through our SmartView portal.
Why choose Cognisys for external infrastructure penetration testing?
We offer a truly comprehensive external infrastructure penetration test by leveraging advanced techniques such as OSINT, subdomain mapping, and dark web credential scanning to uncover vulnerabilities others may miss. Our team not only identifies potential risks but also actively attempts to exploit them, simulating real-world attack scenarios to test your defences. We aim to progress from no external access to achieving internal network access, ensuring a thorough evaluation of your security posture. By combining these efforts with actionable insights and a proven methodology, we deliver unparalleled and thorough testing for your critical external infrastructure.
FAQs
Let’s make things happen
Fill in the form and one of our team will be in touch for a no-obligation discussion or quote regarding your requirements.
info@cognisys.co.uk
Leeds office
5 Park Place
Leeds
LS1 2RU
info@cognisys.co.uk
London office
131 Finsbury Pavement
London
EC2A 1NT