Why do I need wireless penetration testing?
Wireless penetration tests are essential for uncovering vulnerabilities in your WiFi networks, preventing unauthorised access, and safeguarding sensitive data. It ensures compliance with industry regulations and helps organisations avoid emerging security threats.
Regularly assessing your wireless environment can mitigate risks and maintain a robust security posture, protecting your organisation from potential breaches.
Scoping and planning
Define objectives
We work closely with you to define the specific goals of the wireless assessment, whether it’s identifying rogue access points, ensuring secure encryption protocols, or evaluating the overall security of your WiFi infrastructure. This ensures that our testing aligns with your security priorities.
Network overview
We gather a comprehensive overview of your wireless network, including the physical layout, existing access points, and device types. This allows us to understand your network’s structure and identify potential areas of vulnerability.
Compliance requirements
We identify any regulatory or industry standards your wireless network must comply with, such as PCI-DSS or HIPAA. This ensures that our assessment covers all necessary compliance aspects, helping you avoid potential penalties.
Environment preparation
We prepare the testing environment by ensuring all necessary tools and equipment are in place. This includes securing access to your network and setting up any required monitoring systems to test your wireless security accurately.
Tailored testing approach
Our testing approach is customised based on your specific wireless environment and security needs. We ensure our methods are appropriate for your network’s complexity and any unique challenges it presents.
Stakeholder communication
We maintain clear communication with key stakeholders throughout the planning phase, keeping you informed about the assessment’s scope, objectives, and any potential challenges. This ensures alignment and transparency before testing begins.
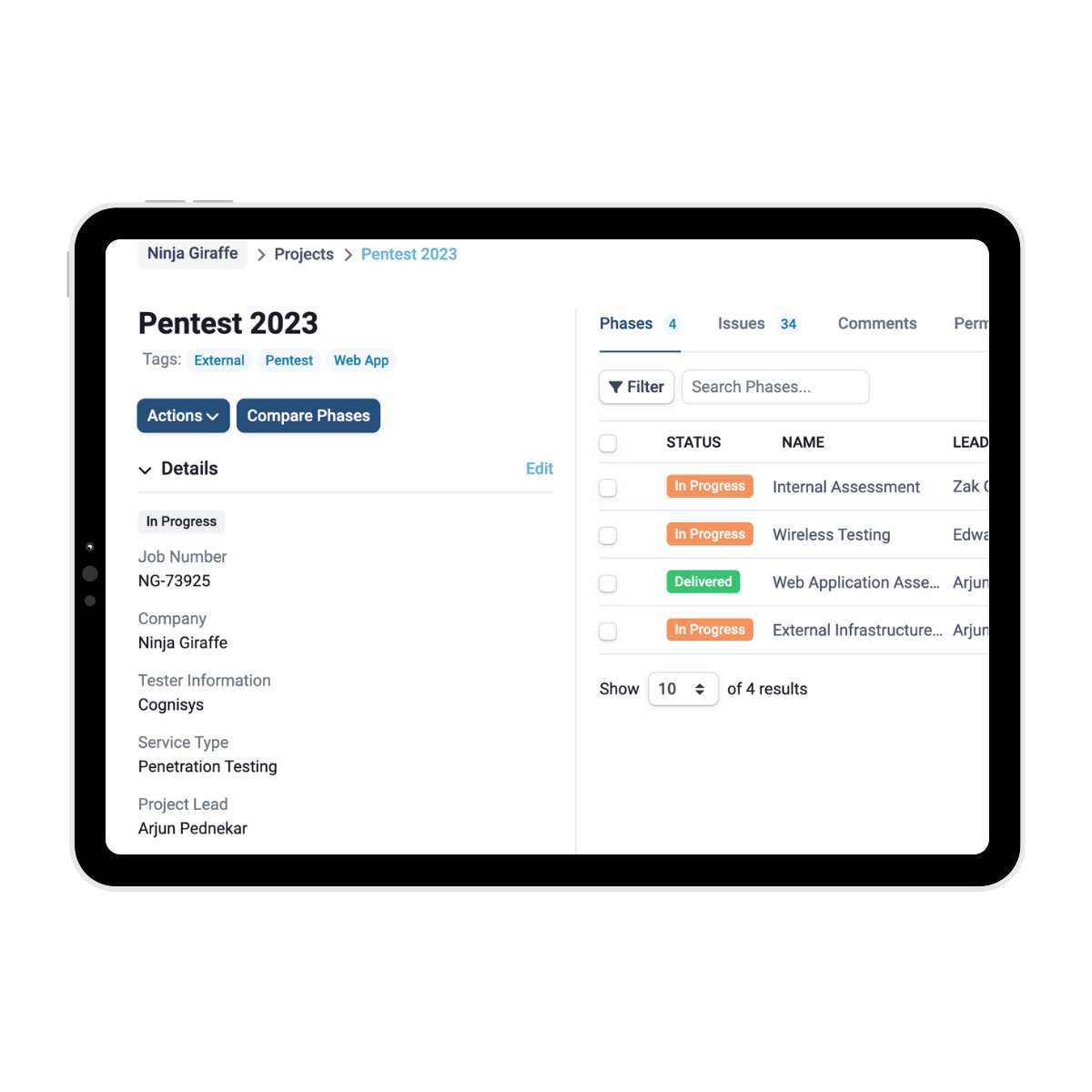
SmartView takes care of your reporting
Cognisys’ SmartView Portal provides a centralised platform for clients to manage their projects and vulnerabilities efficiently. Through the portal, clients can track the status of each identified issue, assign tasks to team members, and monitor the progress of remediation efforts.
A detailed report is prepared once the wireless infrastructure penetration testing is complete, prioritising findings and providing strategic, actionable recommendations to strengthen the external security posture through our SmartView portal.
Why choose Cognisys for wireless penetration testing?
When it comes to securing your WiFi network, our unmatched expertise sets us apart. With a proven track record and a team of certified professionals, we deliver comprehensive wireless assessments that precisely identify and provide recommendations for potential vulnerabilities. Our tailored approach ensures full compliance with industry standards and offers robust protection against emerging threats.
FAQs
Let’s make things happen
Fill in the form and one of our team will be in touch for a no-obligation discussion or quote regarding your requirements.
info@cognisys.co.uk
Leeds office
5 Park Place
Leeds
LS1 2RU
info@cognisys.co.uk
London office
131 Finsbury Pavement
London
EC2A 1NT